For last few days, I was trying to figure out how to set file system auditing via command line. I was looking for this as I had to apply some specific audit policy on multiple file servers. From GUI, we could do this, but it will take hours of manual activity.
As requirement, I had to set Success Audit policy on Delete subfolders and files, delete and change permission.
There are multiple tools available, but none of them have ability to apply specific policy, so I decided to try PowerShell, and finally able to apply those audit policy successfully.
Step-By-Step:
First you have to determine the proper FileSystemRights to apply Audit Policy, and to do that create a test folder and apply required permission. Here I created one test folder in called AuditTest, and gave Delete subfolders and files, delete and change permission to Everyone group.
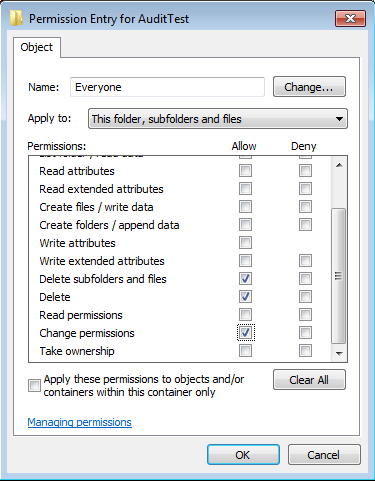
Now to find out the FileSystemRights, open PowerShell and execute the following commands.
$acl = Get-Acl -Path C:AuditTest
$acl.Access
So, my required FileSystemRights for applying Audit Policy are DeleteSubdirectoriesAndFiles, Delete, ChangePermissions, Takeownership.
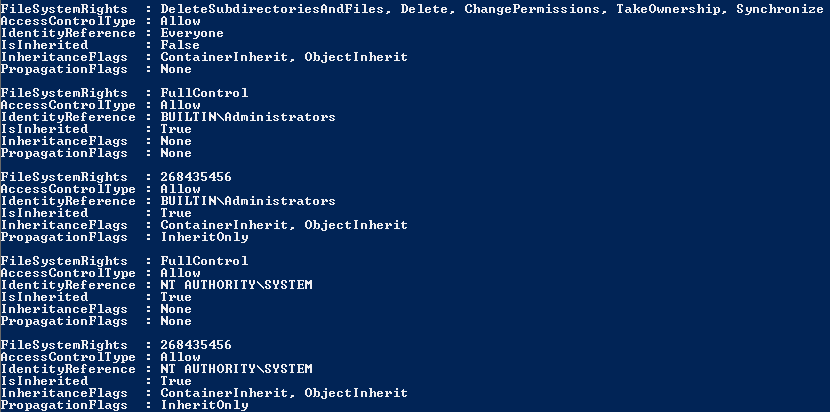
Once I got the FileSystemRights, I use following script to apply Audit Policy. I kept all the location with full path in a txt file (Input.txt) in C drive, and executed the following script.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
$TargetFolders = Get-Content C:\Input.txt $AuditUser = "Everyone" $AuditRules = "Delete,DeleteSubdirectoriesAndFiles,ChangePermissions,Takeownership" $InheritType = "ContainerInherit,ObjectInherit" $AuditType = "Success" $AccessRule = New-Object System.Security.AccessControl.FileSystemAuditRule($AuditUser,$AuditRules,$InheritType,"None",$AuditType) foreach ($TargetFolder in $TargetFolders) { $ACL = Get-Acl $TargetFolder $ACL.SetAuditRule($AccessRule) Write-Host "Processing >",$TargetFolder $ACL | Set-Acl $TargetFolder } Write-Host "Audit Policy applied successfully." |
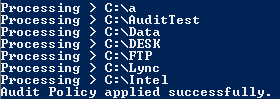
Once you execute the script, you will get following progress list, and wait till finish.
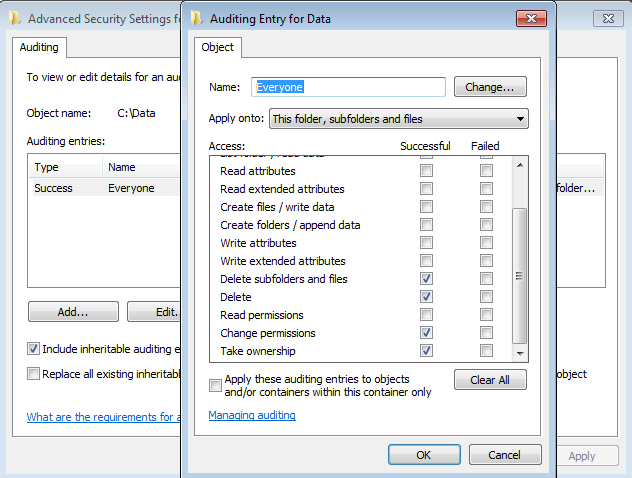
Finally verify the applied policy from GUI.
Update : Now script will only modify Audit details, not overwriting the access permission.
How to Automate GPO Tasks in Active Directory: PowerShell Techniques with Practical Examples
Automating Group Policy Object (GPO) tasks in Active Directory is critical for…

From The Blinking Cursor to The Thinking Machine: A Memoir of Automation
There is a specific kind of silence that only exists in a…

Microsoft Adds Native System Monitor (Sysmon) Support to Windows 11
Microsoft has begun shipping System Monitor (Sysmon) as a native, opt-in capability…

Understanding GPO Inheritance and Blocking: Troubleshooting in Windows Domain Environments
Group Policy Objects (GPOs) are the backbone of centralized management in Windows…
Excellent
Sets audit rules correctly, but unfortunately, this clear also all rights to this directories!
Just remore the $ACL related lines from the script and run again.. it ll not remove the already assigned rights.
Correct.
What do you mean by removing the $ACL lines? Can you elaborate please?
Hi James,
Really sorry for not updating the script earlier.
Now I have updated the script, and it no longer overwriting the existing access permission, will only modify the Audit settings.
Regards,
Saugata D
It’s removing permissions from the Folder/Drive in interest, in my case i need to enable failure audit for C: Drive.
However it’s running okay when i re-added those removed user’s from Permission’s Tab & if i am Rerunning, it’s working okay.
Below is the syntax i am using:
$TargetFolders = “C:”
$AuditUser = “Everyone”
$AuditRules = “FullControl”
$InheritType = “None”
$AuditType = “Failure”
$AccessRule = New-Object System.Security.AccessControl.FileSystemAuditRule($AuditUser,$AuditRules,$InheritType,”None”,$AuditType)
foreach ($TargetFolder in $TargetFolders)
{
$ACL = (Get-Item $TargetFolder).GetAccessControl(‘Access’)
$ACL.SetAuditRule($AccessRule)
Write-Host “Processing >”,$TargetFolder
$ACL | Set-Acl $TargetFolder
}
Write-Host “Audit Policy applied successfully.”
I am not sure why it is not working in your environment, I have tested the code again, and everything seems to be working as expected here. It is only updating the audit policy not the existing permissions.
Please make sure your are the member for the local Administrators group.
This is really useful, thanks! Do you know if there is a way to get this to update Windows ‘Protected’ folders such as c::\windows\system32, c:\windows\syswow64, etc? I get ‘PermissionDenied’ when running this on those types of folders.
Thanks!
You have to use SubInACL tool for that, I hope it will able to update the ACL for those protected files.
Check this : https://technochat.in/2013/11/ntfs-permission-issue-with-takeown-icacls/
This script is almost exactly what I need. But I’m new to PowerShell, and I’m not sure how you generated Input.txt. How would I make an Input.txt that includes every file on a drive? Or does the script know how to recurse? Or is there a better way?
You just have to put the folder names with path each line on input file. for eg. if you want to apply the audit to some folders on D drive, the it will be like
D:\Yourfolder1
D:\Yourfolder2
D:\Yourfolder3
D:\Yourfolder3
Will this work on setting audits on file(s) in system32 and SysWOW64 folders. For example:
\%Windows%\System32\activeds.dll
I need to set Failed events.
Thanks!
I guess it will work, you could give it a try and let us know.
regards,
Saugata D
Saugata,
Is there a way to tick the box where it says ‘only apply these auditing settings to objects and / or containers within this container’
I never tried that, but I guess you can also find it out your own, just create a test folder and take the permission snap into a variable, then made the changes manually and take another permission snap in to new variable, and the compare them,. i guess you will able to find out what you are looking for.
before
$acl1 = Get-Acl -Path C:\AuditTest
After
$acl2 = Get-Acl -Path C:\AuditTest
Hello
I accidentally used the “Contact us” option instead of scrolling down. I apologize.
The script works great even on protected folders. My questions is, if it is possible to modify the Audit parameter “Applies to” and set it to “This Folder only”???
Kind Regards
It’s fine mate, I don’t think you can do it, but you can change the inheritance type.
$InheritType = “ContainerInherit,ObjectInherit”
how to run auditing failure to everyone for multiple servers
I really didn’t understand what you are looking for, could you please explain it in details.
Hi,
I tried this script it works much better. but in my case the audit policy is not applied for subfolders and files the folders which applied the audit policy.
Inherit type i write is same ie., $InheritType = “ContainerInherit,objectInherit” and i in prompt it also shows that “apply onto: ‘this folder,subfolder and files.'”
but when i tick on “Replace all existing inheritable auditing entries on all descendants with inheritable auditing entries from this object” then its apply on subfolders and files within it.
so how can i tick on this programatically. i search on net but cant get any solution will do the same.
Thanks in advanced. 🙂
I didn’t get a chance to validate this right now, but for the time being you cane use the following to get all the folders as input file and then execute.
(Get-ChildItem -Recurse| ? {$_.PSIsContainer}).FullName
ok,
Thanks You. Saugata 🙂
can you show me Input.txt, what are the location need to mentioned
Hi,
If you are using this script without modifying anything, you have to put your input file in C:\Input.txt
And this the Input.txt file, you have to mention the full path of the target folders each line, for eg.
C:\abc
C:\xyz
D:\abc
D:\xyz
Regards,
Saugata D.
Hello Sir,
How can i check applies to setting means which command will show apply to setting example : this folder and subfolders or the files only of the folder auditing.
Hay,
sorry for delayed response, please read my next reply to understand.
Hi
how can i applies to “This folder only”
You have to find it yourself by,
01. Creating a test folder. (C:\AuditTest)
02. Then log its permission details from PowerShell ($aclBefore = Get-Acl -Path C:\AuditTest)
03. Apply required permission from GUI.
04. Then again log its permission details from PowerShell. ($aclAfter = Get-Acl -Path C:\AuditTest)
05. Finally comparing both the logged permissions to understand what parameters you need. ($aclBefore.Access and $aclBefore.Access)
Hi Sagunta,
I need ur help here urgently.
We are trying to enable auditing for around 2000 servers to below mentioned folder & files in win 2k8 servers, While applying we are getting error as below.
Set-Acl : Cannot bind argument to parameter ‘Path’ because it is an empty string.
At line:13 char:26
+ $ACL | Set-Acl -path $TargetFolder
+ ~~~~~~~~~~~~~
+ CategoryInfo : InvalidData: (:) [Set-Acl], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationErrorEmptyStringNotAllowed,Microsoft.PowerShell.Commands.SetAclCommand
Get-Acl : Cannot validate argument on parameter ‘Path’. The argument is null or empty. Provide an argument that is not null or empty, and then try the command again.
At line:10 char:26
+ $ACL = Get-Acl -Path $TargetFolder
+ ~~~~~~~~~~~~~
+ CategoryInfo : InvalidData: (:) [Get-Acl], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationError,Microsoft.PowerShell.Commands.GetAclCommand
Processing >
Set-Acl : Cannot bind argument to parameter ‘Path’ because it is an empty string.
At line:13 char:26
+ $ACL | Set-Acl -path $TargetFolder
+ ~~~~~~~~~~~~~
+ CategoryInfo : InvalidData: (:) [Set-Acl], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationErrorEmptyStringNotAllowed,Microsoft.PowerShell.Commands.SetAclCommand
Folder Name :
C:\bootmgr
C:\Windows\system32
C:\Windows\syswow64
C:\Windows\
C:\Windows\system32\winload.exe
Could you please help me on this. It will be really grateful.
The script does its job but when I try to change the $AuditType variable from “Success” to “All” it doesn’t change, always keeping “Success” showing a structure error in the line $AccessRule = New-Object …..
It is correct to modify this variable if you want Auditing consider both Failures and Success?