Guardian is an open-source, AI-driven penetration testing framework that leverages multiple large language models to automate intelligent, evidence-backed security assessments. Designed for enterprise use, it combines a multi-agent architecture with a broad toolset to accelerate reconnaissance, triage, and reporting while preserving human oversight.
What is Guardian?
Guardian is an AI-powered penetration testing automation framework developed by Zakir Kun and available on GitHub. It orchestrates models such as OpenAI GPT-4, Anthropic Claude, Google Gemini, and OpenRouter in a unified, multi-agent pipeline to perform adaptive security testing with full evidence capture.
Multi-Agent Architecture
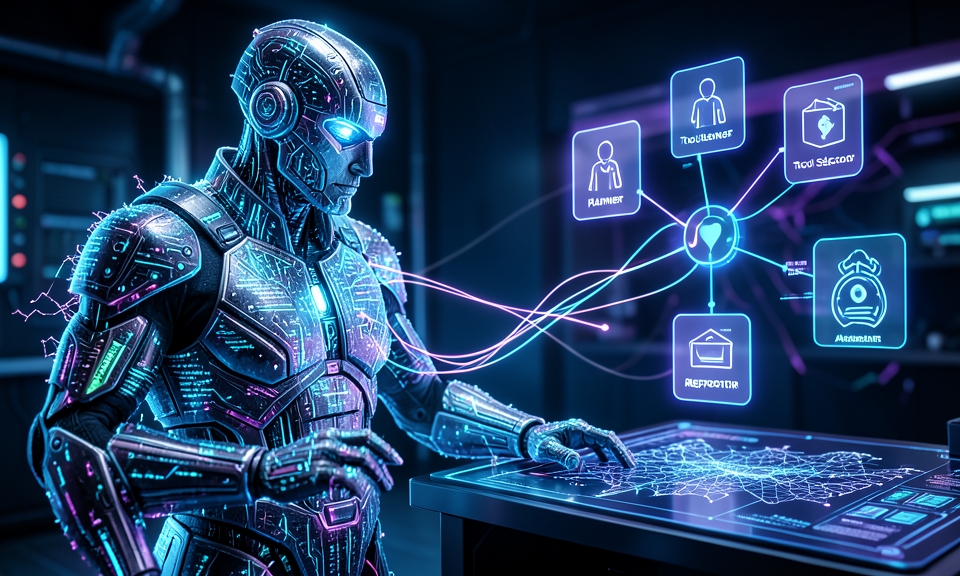
Rather than treating AI as a passive helper, Guardian assigns specialized roles to agents that collaborate throughout an engagement. This teamwork-driven design enables dynamic decision-making and iterative testing that mimics an experienced human pentester.
- Planner: Crafts the assessment strategy and priorities.
- Tool Selector: Chooses which integrated security tools to invoke based on context and objectives.
- Analyst: Interprets findings, filters false positives, and refines follow-up actions.
- Reporter: Compiles professional, reproducible reports including raw outputs and AI decision traces.
19-Tool Arsenal
Guardian integrates 19 widely used security tools across network, web, discovery, scanning, and analysis domains. The framework adapts to available tools and can run multiple tools in parallel to shorten engagement time while maintaining coverage.
- Nmap — Comprehensive port scanning and service detection.
- Masscan — Ultra-fast large-scale port scanning.
- httpx — HTTP probing and response analysis for web reconnaissance.
- WhatWeb — Technology fingerprinting for websites.
- Wafw00f — Web Application Firewall (WAF) detection.
- Subfinder — Passive subdomain enumeration.
- Amass — Active and passive network mapping and subdomain discovery.
- DNSRecon — DNS enumeration and analysis.
- Nuclei — Template-based vulnerability scanning.
- Nikto — Web server vulnerability scanning.
- SQLMap — Automated SQL injection detection and exploitation.
- WPScan — WordPress-specific vulnerability scanning.
- TestSSL — SSL/TLS cipher suite and protocol analysis.
- SSLyze — Advanced SSL/TLS configuration analysis.
- Gobuster — Directory and file brute-forcing for content discovery.
- FFuf — Advanced web fuzzing.
- Arjun — HTTP parameter discovery.
- XSStrike — Advanced XSS detection and exploitation.
- GitLeaks — Secret and credential scanning in repositories.
Flexible, Reproducible Workflows
Guardian ships with predefined workflows—Recon, Web, Network, and Autonomous—that are fully configurable through YAML. Workflow-level settings override central configuration files, which in turn override tool defaults, enabling parallel engagements with independent configurations and repeatable results.
Reports are produced in Markdown, HTML, or JSON and include raw tool output, AI decision traces, executive summaries, and 2,000-character evidence snippets that link findings back to originating commands for full session reconstruction.
Safety-First Design
Guardian includes built-in safeguards to support authorized use and minimize accidental or destructive operations. These mechanisms help maintain ethical and legal boundaries during automated assessments.
- Scope validation automatically blacklists private RFC-1918 address ranges.
- Safe mode prevents destructive actions by default.
- Configurable confirmation prompts create human-in-the-loop checkpoints for sensitive operations.
- Comprehensive audit logging captures AI decisions and command histories for post-engagement review.
Requirements and Roadmap
Guardian requires Python 3.11 or higher and at least one AI provider API key to function. It supports environment variable-based key management across Linux, macOS, and Windows. Released as version 2.0.0, the project outlines an ambitious roadmap to improve usability and integrations.
- Web dashboard for visualizing engagements and results.
- PostgreSQL backend support for multi-session tracking.
- MITRE ATT&CK mapping for structured findings.
- Plugin architecture for community extensions and CI/CD integration.
- Support for additional models such as Llama and Mistral.
Responsible Use and Ethical Considerations
While Guardian streamlines penetration testing, teams must enforce strict governance: secure explicit authorization before testing, configure scope and safe-mode controls properly, and maintain human oversight of automated decisions to prevent misuse.
Practical Applications
Guardian is suited for a variety of security contexts where reproducible, evidence-backed testing accelerates work and preserves audit trails.
- Red teams and pentesters who want to accelerate reconnaissance and triage while preserving evidence trails.
- Security teams that require reproducible, automated assessments integrated into CI/CD pipelines.
- Educational labs where learners can observe automated workflows and evidence-backed reporting.
- Researchers building defensive strategies based on reproducible attack simulations.
Conclusion
By blending a multi-agent AI architecture with a comprehensive toolset and layered safety controls, Guardian advances automated penetration testing to be smarter, faster, and more auditable—while emphasizing the human-in-the-loop safeguards necessary for ethical use.