
Microsoft has begun shipping System Monitor (Sysmon) as a native, opt-in capability in Windows 11 preview builds. This change moves a widely used, high-fidelity endpoint telemetry tool from an optional Sysinternals download to an OS-managed feature. For security teams, IT operations, and incident responders, native Sysmon promises simpler deployment, stronger integration with Windows management channels, and a more consistent telemetry baseline across managed fleets — provided organizations adopt it carefully and treat configurations as code. Below I unpack the technical details, operational implications, enablement steps, detection benefits, and practical recommendations for pilots and enterprise rollouts.
What Sysmon does and the telemetry signals it provides
Sysmon (System Monitor) has been a staple of Windows endpoint visibility for years. Architecturally it runs as a service with a kernel-level driver and writes structured events to the Windows Event Log. The value proposition is straightforward: Sysmon captures contextual telemetry that the OS’s default logs typically do not, producing events that contain reliable fields analysts can use for hunting and incident response. At a minimum, Sysmon records process creation and termination with command-line arguments and parent process identifiers — data that lets investigators trace execution chains and identify living-off-the-land techniques. Beyond that, administrators can configure Sysmon to log file creation and modification, image and driver loads, registry changes tied to persistence behaviors, named-pipe and mutex activity, and network connections correlated to process IDs. It also supports optional binary hashing, which provides immutable indicators for post-incident attribution and automated blocking. These structured events integrate seamlessly with SIEMs, EDR platforms, and custom analytics engines, enabling deterministic correlations such as linking a suspicious network connection to the exact process and command line that opened it. The configurability — via XML rule sets — is a core strength: teams control which events to capture, filter known benign noise (for example, excluding telemetry from trusted vendor updaters), and balance fidelity with performance. That configurability makes Sysmon suitable for both broad telemetry collection and targeted forensic capture, depending on organizational priorities and resource constraints.
How native integration changes delivery, governance, and management
Embedding Sysmon into Windows 11 changes how organizations acquire, update, and manage this capability. Historically, Sysmon required a separate download and installer from the Sysinternals site. That model introduced operational friction: distribution, version control, and driver management had to be handled by endpoint management tooling. With native Sysmon, Microsoft delivers the capability through the OS image and Windows servicing pipeline. Management surfaces include the Settings UI in preview builds and scripted enablement via DISM and PowerShell, making it easier to flip the feature on at scale. This shift brings two important governance outcomes. First, a first-party component benefits from Windows platform protections such as code integrity and the OS update cadence — reducing certain risks associated with third-party binaries being tampered with or left unpatched. Second, centralized delivery simplifies lifecycle management; feature updates and fixes can flow with Windows updates rather than separate installers. Microsoft has chosen an opt-in model with native Sysmon disabled by default. This design prevents unintentional log storms and gives administrators explicit control over when telemetry collection begins. Importantly, Microsoft requires that any standalone Sysmon installation be uninstalled before enabling the native implementation to avoid driver and event-channel conflicts. For many enterprises, this will require scripted removal of legacy installs followed by controlled enablement and configuration deployment via Intune, Configuration Manager, or Group Policy automation.
Enabling native Sysmon: recommended steps and operational safeguards
Enabling native Sysmon in Windows 11 preview builds should follow a deliberate process that minimizes risk to production workloads. High-level operational steps include:
- Inventory and uninstall any legacy Sysmon instances obtained from Sysinternals to prevent conflicts;
- Enable the native feature through the Settings UI in preview builds or via DISM/PowerShell for automated rollouts;
- Initialize the service and deploy a vetted XML configuration that defines which events and filters to apply;
- Validate ingestion into downstream collectors and adjust SIEM parsing rules; and
- Monitor performance and event volume closely during pilot phases.
Treat Sysmon configuration as code: store XML configs in version control, subject changes to review, and maintain a change log tied to your change-control process. Start with conservative community-vetted baselines, then iterate. Key tuning areas: exclude high-volume, low-value sources (software updaters, telemetry agents), be cautious with full binary hashing (CPU and I/O cost), and limit file creation logging on busy file servers unless necessary for forensic reasons. Ensure your log pipeline can handle the increased volume: scale collectors, tune ingestion rules, and revise retention tiers to maintain both performance and compliance. Finally, prepare rollback playbooks that disable the feature and revert to a prior configuration quickly if you see system degradation; include health checks that track CPU, I/O, and event throughput to provide objective rollback criteria.
Security and detection benefits of native Sysmon
Native Sysmon materially improves endpoint visibility and can elevate detection engineering across an estate. By lowering adoption barriers, more endpoints—especially those historically constrained from installing extra utilities—can produce consistent high-fidelity telemetry. Consistent schemas and fields across machines simplify writing portable detection rules and make hunting queries far more reliable. For detection teams, Sysmon supplies deterministic signals: parent-child process chains, detailed command-line arguments, process-to-network mappings, DLL and driver load events, and file-hash evidence. These signals enable more accurate correlation of suspicious chains of activity and reduce blind spots that attackers exploit. From an operational perspective, first-party delivery reduces some tampering vectors: OS-managed components are more amenable to code-integrity controls and Windows update trust chains than separately installed agents. However, native Sysmon is an augmentation, not a replacement, for layered security: robust EDR, identity protections, network monitoring, and zero-trust controls remain essential. The real security value emerges when Sysmon events are woven into alerting and playbooks—when detection engineering uses these fields to triage and automate responses, and incident responders can pivot quickly from a single enriched event to a full picture of an intrusion.
Pilot design and enterprise adoption recommendations
Adopt native Sysmon through a staged, data-driven approach. Begin with a pilot that spans representative device classes: knowledge-worker endpoints, developer machines, and servers that reflect diverse workloads. During the pilot measure CPU, memory, and disk I/O impact; monitor event volumes forwarded to your SIEM; and validate that existing detection rules and playbooks work with the new event streams. Use community rule-sets as a starting point but harden them for your environment — add exclusions for trusted vendor processes and tune thresholds for high-volume events. Automate configuration distribution and lifecycle management using Intune, Configuration Manager, or scripted group policy objects. Treat configuration changes as part of your change-control and incident response documentation, and include rollback steps in runbooks. Ensure the logging architecture is prepared: scale collectors, revise ingestion parsers, and set retention policies that meet forensic and compliance requirements. Communicate with stakeholders — sysadmins, app owners, business units — about potential impacts and provide a narrow-window pilot timeline with clear rollback criteria. Finally, watch Microsoft guidance and Windows Insider notes: the feature is currently available in preview builds (Windows 11 Preview Build 26220.7752 (KB5074177) and 26300.7733 (KB5074178)), and implementation details may evolve before general availability. With a methodical rollout — pilot, measure, tune, automate, scale — native Sysmon can significantly raise baseline observability without imposing untenable operational burden.
How to Automate GPO Tasks in Active Directory: PowerShell Techniques with Practical Examples
Automating Group Policy Object (GPO) tasks in Active Directory is critical for…
Task Scheduler Error “A specified logon session does not exist” – Fix via Command Line and PowerShell for Scripting
This is very know issue, if you search internet, you will get…

India AI Impact Summit 2026 — Global AI Leadership
India AI Impact Summit 2026 in New Delhi brings together governments, industry,…

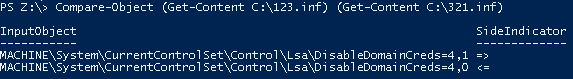
Understanding GPO Inheritance and Blocking: Troubleshooting in Windows Domain Environments
Group Policy Objects (GPOs) are the backbone of centralized management in Windows…