
If you are working on AWS environment and if you follow the news related to AWS, you will probably know there are many major data breach happened because of the human negligence, where vast amount of data kept without any protection like encryption, public access blocking. It is all because of human error. We create S3 bucket, and start using them, without realizing on how to keep them protected.
If we can’t control the human behavior, at least we can do a daily security scan on all the buckets and get the clear picture of how the buckets are configured after creation and how many of the S3 buckets are not following security best practice. If we can get this information, we could easily fix them. So, for this reason I have created one AWS PowerShell script to extract the S3 bucket audit report. This script can be executed anytime, and only need read-only permission.
This script can collect following information for all the S3 buckets.
- Bucket Name
- Region
- Encryption Status
- Log Bucket Name
- Log Bucket Target Prefix
- Versioning Status
- MFA on Delete Status
- Block Public Acls Status
- Ignore Public Acls Status
- Block Public Policy Status
- Restrict Public Buckets Status
- Bucket Policy Configuration Status
- Bucket Policy
Please find the sample report generated by this script.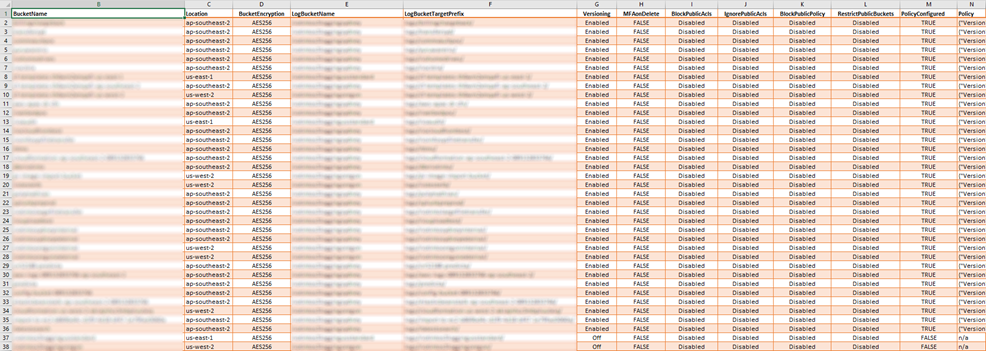
Script:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 | $SessionID = $((Get-Date).ToString("ddmmyyyyhhMMssffff")) #Getting all the S3 Buckets, it should be from us-east-1 to get the correct creation time. $GetAllBuckets = Get-S3Bucket -Region us-east-1 $getS3list = @() foreach ($OneBucket in $GetAllBuckets) { $BucketLocation = $((Get-S3BucketLocation $OneBucket.BucketName).Value) $OneBucket | Add-Member @{Location=if($BucketLocation){$BucketLocation}else{"us-east-1"}} -Force $getS3list += $OneBucket } #Searching target S3 bucket $MyS3Data = @() foreach ($s3 in $getS3list) { $GetPolicyStatus = (Get-S3BucketPolicy $($s3.BucketName) -Region $($s3.Location)) $GetPubAccess = try{Get-S3PublicAccessBlock -BucketName $($s3.BucketName) -Region $($s3.Location)}catch{} $Logging = Get-S3BucketLogging -BucketName $($s3.BucketName) -Region $($s3.Location) $Encryption = (Get-S3BucketEncryption -BucketName $($s3.BucketName) -Region $($s3.Location)).ServerSideEncryptionRules $Versioning = Get-S3BucketVersioning -BucketName $($s3.BucketName) -Region $($s3.Location) $s3 | Add-Member @{LogBucketName = if($Logging.TargetBucketName){$Logging.TargetBucketName}else{"Not Configured"}} -Force $s3 | Add-Member @{LogBucketTargetPrefix = if($Logging.TargetPrefix){$Logging.TargetPrefix}else{"Not Configured"}} -Force $s3 | Add-Member @{Versioning= $Versioning.Status} -Force $s3 | Add-Member @{MFAonDelete = $Versioning.EnableMfaDelete} -Force if($Encryption) { $s3 | Add-Member @{BucketEncryption = $($Encryption.ServerSideEncryptionByDefault.ServerSideEncryptionAlgorithm.Value)} -Force } else { $s3 | Add-Member @{BucketEncryption = "No Encryption"} -Force } $s3 | Add-Member @{PolicyConfigured = if($GetPolicyStatus){$true}else{$false}} -Force $s3 | Add-Member @{PolicyName = if($GetPolicyStatus){$($GetPolicyStatus | ConvertFrom-Json).Id}else{"n/a"}} -Force $s3 | Add-Member @{Policy = if($GetPolicyStatus){$GetPolicyStatus}else{"n/a"}} -Force $s3 | Add-Member @{BlockPublicAcls = if($GetPubAccess){$GetPubAccess.BlockPublicAcls}else{"Disabled"}} -Force $s3 | Add-Member @{IgnorePublicAcls = if($GetPubAccess){$GetPubAccess.IgnorePublicAcls}else{"Disabled"}} -Force $s3 | Add-Member @{BlockPublicPolicy = if($GetPubAccess){$GetPubAccess.BlockPublicPolicy}else{"Disabled"}} -Force $s3 | Add-Member @{RestrictPublicBuckets = if($GetPubAccess){$GetPubAccess.RestrictPublicBuckets}else{"Disabled"}} -Force $MyS3Data +=$s3 } $MyS3Data | select CreationDate,BucketName,Location,BucketEncryption,LogBucketName,LogBucketTargetPrefix,Versioning,MFAonDelete,BlockPublicAcls,IgnorePublicAcls,BlockPublicPolicy,RestrictPublicBuckets,PolicyConfigured,Policy | Export-Csv "$env:USERPROFILE\Desktop\S3Bucket-Audit-$SessionID.csv" -NoTypeInformation |
Disclaimer: All posts and opinions on this site are provided AS IS with no warranties. These are our own personal opinions and do not represent our employer’s view in any way.
This article currently have 4,946 views
![]() This work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License.
This work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License.
Can it also cross reference every IAM policy in the same account, to work out what users/roles/groups have access to any part of the bucket via IAM policies applied to their IAM principle?
That is what I’m looking for. Does your script do that?
Please let me know.
No, script can’t do it. You probably can add those features, but I don’t think it will be much helpful if you have many S3 buckets with lots of data on it. I would suggest to audit all the IAM Roles/Accounts including their shared or in-line policies, as you can easily understand what level of access someone have on S3 bucket by checking the IAM policy. If you are doing using PowerShell, you could use ConvertFrom-Json / ConvertTo-Json for reading JSON policy easily.
Regards,
Saugata D.
thanks, this was really helpful and just what I needed!
You welcome.